SSH (Secure Shell) is a cryptographic network protocol that permits safe distant entry to a server over an insecure community. It is commonly used to access and handle servers, transfer recordsdata, and carry out other distant duties. In this text, we are going to explore the way to use SSH to hook up with a distant server. Secure Shell (SSH) is a cryptographic community protocol used for safe communication and distant command execution between computers.
- Rsync also can preserve file permissions, timestamps, and symbolic hyperlinks, making it ideal for comprehensive backups.
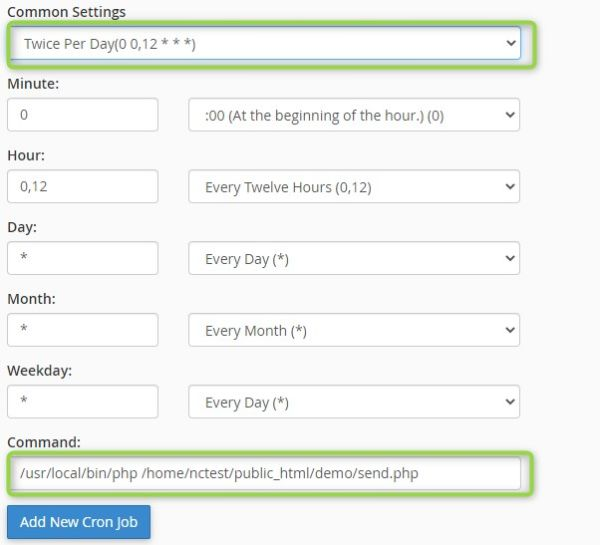
- Consult a PHP growth company if you need professional assist with the upkeep of the PHP SSH server setup.
- Learn about SSH file switch, its advantages, and the means it works.
- In this part, we’ll undergo the steps of enhancing information over SSH using nano.
- This could be particularly useful when you have a lot of files organized in a listing structure that you simply wish to transfer.
- We’ll show you the steps to use a particular command (think of it like a secret handshake) to attach your pc to a faraway server in the world of Linux.
Tips On How To Setup Sftp Public Key Authentication On The Command Line
This will copy check.txt from your local Paperwork listing to the /home/jane/ directory on the distant server. In the following section, let’s take a look at tips on how to use SSH for secure remote access in Ubuntu. I guess you forgot to mention you’ll find a way to disable password authentication after setting up SSH keys, as to not be uncovered to brute drive attacks.
Transferring Information Using Ssh
Transferring information around securely is extra necessary than ever, and SSH gives you that security AvaHost with out making issues difficult. Not Like old-school FTP or downloading and reuploading files manually, SSH-based transfers keep your information encrypted from start to finish. Yes, you should use PHP to run scripts on a remote server by way of SSH.
Ssh Key Authentication Errors
If your web connection is shared with other customers or gadgets, ensure that there aren’t any bandwidth-intensive activities occurring concurrently. Consider connecting to a quicker or more steady network if potential. One common permission concern is inadequate privileges to access or modify files on the remote server.